Website DDoS Protection & Mitigation
Guarantee your website availability and performance against the largest attacks.
Built for all platforms and custom sites
All plans include.
Layer 3 & 4 Attacks
NexonHost DDoS Protection and Mitigation comes with up to 40Gbps DDoS Protection included on all dedicated server plans.
Machine Learning
Attack data is systematically correlated to predict malicious behavior and safeguard against emerging threats.
High Performance Hardware
Our platform guarantees performance by utilizing premium hardware and high quality technology.
24/7 Support
Seamless operations with 24/7 expert assistance for your servers. From setup to troubleshooting, we've got you covered.
Analytics and Reports
Complex statistics and detailed reports on mitigated attacks are available in your Client Area.
Premium Network
Our network has redundant Tier-1 Providers with multiple failover systems in place, traffic reaches us to the shortest paths available.
Protect your website
Reverse proxy DDoS protection for Layer 4 & 7 attacks — fast, reliable, and always on.

Micro
35% Discount
Triennially Payment
After the 1TB clean bandwidth limit is reached, the proxy plan will be limited to 20Mbps
If the attack goes above 10Gbps, the Micro proxy plan will be suspended until the attack is over.

Small
35% Discount
Triennially Payment
After the 3TB clean bandwidth limit is reached, the proxy plan will be limited to 50Mbps
If the attack goes above 25Gbps, the Small proxy plan will be suspended until the attack is over.

Business
35% Discount
Triennially Payment
After the 10TB clean bandwidth limit is reached, the proxy plan will be limited to 200Mbps
If the attack goes above 50Gbps, our team will inform you about the size of the attack and the possibility of an upgrade if the attack is persistent.

Enterprise
35% Discount
Triennially Payment

Micro
20% Discount
Biannually Payment
After the 1TB clean bandwidth limit is reached, the proxy plan will be limited to 20Mbps
If the attack goes above 10Gbps, the Micro proxy plan will be suspended until the attack is over.

Small
20% Discount
Biannually Payment
After the 3TB clean bandwidth limit is reached, the proxy plan will be limited to 50Mbps
If the attack goes above 25Gbps, the Small proxy plan will be suspended until the attack is over.

Business
20% Discount
Biannually Payment
After the 10TB clean bandwidth limit is reached, the proxy plan will be limited to 200Mbps
If the attack goes above 50Gbps, our team will inform you about the size of the attack and the possibility of an upgrade if the attack is persistent.

Enterprise
20% Discount
Biannually Payment

Micro
10% Discount
Annually Payment
After the 1TB clean bandwidth limit is reached, the proxy plan will be limited to 20Mbps
If the attack goes above 10Gbps, the Micro proxy plan will be suspended until the attack is over.

Small
10% Discount
Annually Payment
After the 3TB clean bandwidth limit is reached, the proxy plan will be limited to 50Mbps
If the attack goes above 25Gbps, the Small proxy plan will be suspended until the attack is over.

Business
10% Discount
Annually Payment
After the 10TB clean bandwidth limit is reached, the proxy plan will be limited to 200Mbps
If the attack goes above 50Gbps, our team will inform you about the size of the attack and the possibility of an upgrade if the attack is persistent.

Enterprise
10% Discount
Annually Payment

Micro
5% Discount
Semi Annually Payment
After the 1TB clean bandwidth limit is reached, the proxy plan will be limited to 20Mbps
If the attack goes above 10Gbps, the Micro proxy plan will be suspended until the attack is over.

Small
5% Discount
Semi Annually Payment
After the 3TB clean bandwidth limit is reached, the proxy plan will be limited to 50Mbps
If the attack goes above 25Gbps, the Small proxy plan will be suspended until the attack is over.

Business
5% Discount
Semi Annually Payment
After the 10TB clean bandwidth limit is reached, the proxy plan will be limited to 200Mbps
If the attack goes above 50Gbps, our team will inform you about the size of the attack and the possibility of an upgrade if the attack is persistent.

Enterprise
5% Discount
Semi Annually Payment

Micro
0% Discount
Monthly Payment
After the 1TB clean bandwidth limit is reached, the proxy plan will be limited to 20Mbps
If the attack goes above 10Gbps, the Micro proxy plan will be suspended until the attack is over.

Small
0% Discount
Monthly Payment
After the 3TB clean bandwidth limit is reached, the proxy plan will be limited to 50Mbps
If the attack goes above 25Gbps, the Small proxy plan will be suspended until the attack is over.

Business
0% Discount
Monthly Payment
After the 10TB clean bandwidth limit is reached, the proxy plan will be limited to 200Mbps
If the attack goes above 50Gbps, our team will inform you about the size of the attack and the possibility of an upgrade if the attack is persistent.

Enterprise
0% Discount
Monthly Payment

FLEXIBLE AND SCALABLE
From micro to enterprise
PHP Hosting
Choose a managed hosting service for high-performing sites.
WordPress Hosting
Check out our blazing fast WordPress DDoS protected hosting plans.
SIMPLE AND INTUITIVE
User-Friendly Control Panel
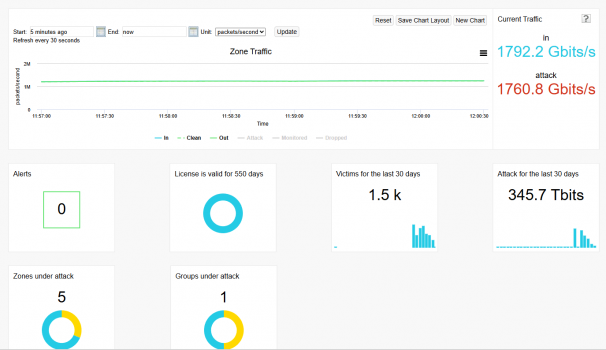
Manage your website DDoS Protection modules and check out the attack statistics
Powerful
Manage your Website sites easily and with more freedom.
Complex
Secure your plan to the finest steps

SUPPORT & GUIDANCE
24/7 support
NexonHost supports thousands of websites and applications worldwide.
Our technical experts will help you manage your business as when needed.
DDoS protection features
Frequently Asked Questions
What is Remote DDoS Protection?
Remote DDoS Protection diverts your website traffic through a highly secure network before reaching your server. This network filters out malicious traffic, ensuring only legitimate visitors access your website. Think of it as a security checkpoint for your website, safeguarding it from online threats.
What is required to get set up with remote DDoS protection?
The setup process is typically straightforward. NexonHost will guide you through the steps, which may involve some configuration changes on your domain name registrar side. Our technical support team is readily available to assist you throughout the process.
What can a Remote DDoS Protection be used for?
Remote DDoS Protection Plans are a valuable security investment for a wide range of websites. From e-commerce platforms facing high traffic volumes during sales to online gaming servers targeted by malicious actors, DDoS attacks can disrupt critical services and cause financial losses. Financial institutions safeguarding sensitive data, news and media websites ensuring the free flow of information, and government agencies providing essential services to citizens all require robust protection against these attacks. Even high-profile websites or those handling sensitive data can benefit from DDoS mitigation, ensuring continued online presence and data security.
What is the suitable Remote DDoS Protection plan for you?
The ideal plan depends on your website’s traffic volume and the type of content you host. For instance, an e-commerce platform with high daily transactions would require a more robust plan compared to a personal blog. Our sales team can help you assess your needs and recommend the most appropriate solution.
Can NexonHost's DDoS protection plans protect my business from all cyberattacks?
While DDoS protection is crucial, it’s one part of a comprehensive cybersecurity strategy. NexonHost offers additional security solutions like Web Application Firewalls (WAF) to further fortify your online defenses. Additionally, maintaining good security practices like keeping your software updated and using strong passwords is essential.
Is NexonHost's DDoS protection expensive?
NexonHost offers a range of DDoS protection plans to fit various budgets. We believe robust security shouldn’t be a luxury, and our plans are competitively priced to make them accessible for businesses of all sizes.
Custom Quote
If the DDoS protected plans we have above do not fit your needs, please message us and we will create a custom plan for you and your enterprise.
